TECHNOLOGIES
SOLARNETHUB
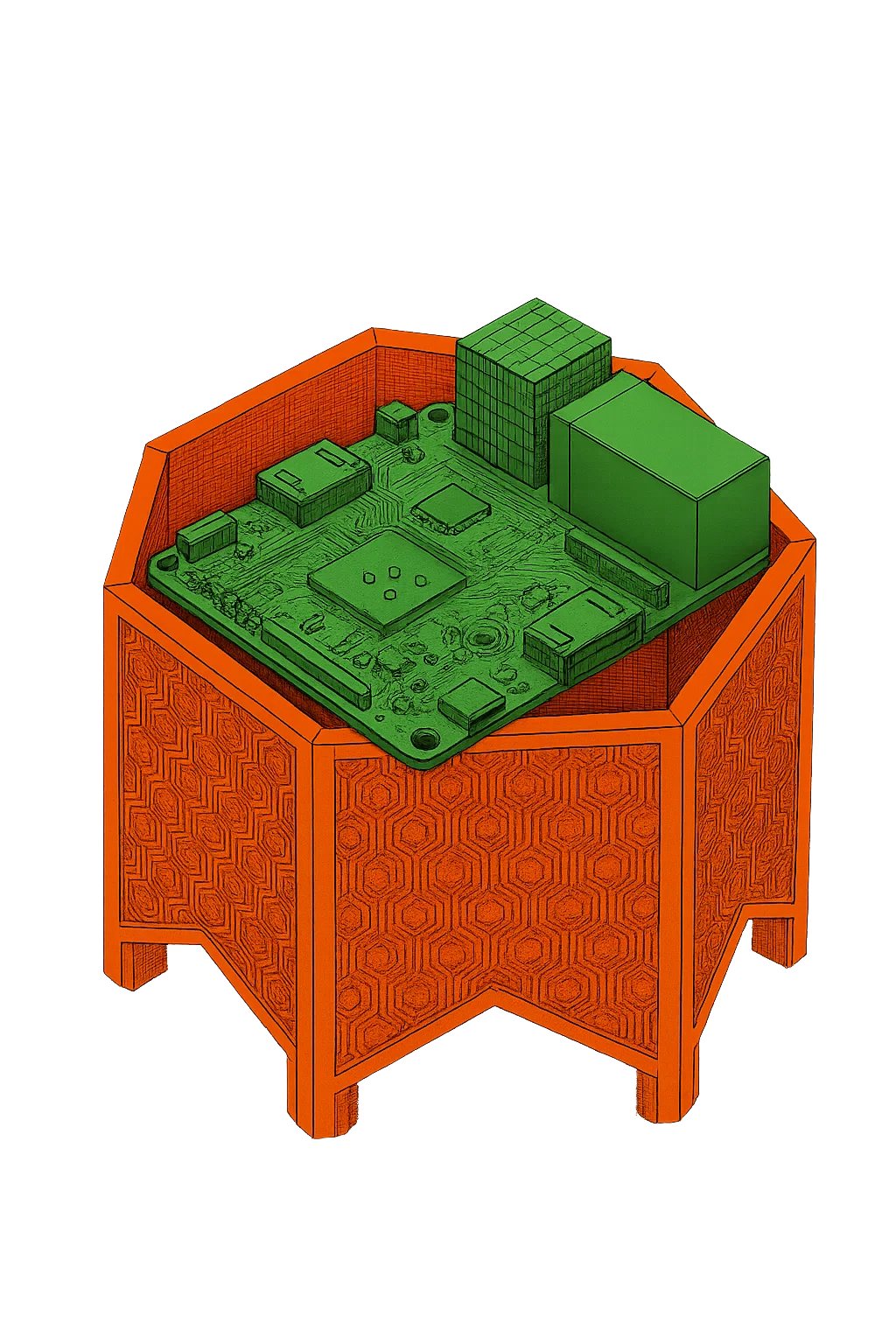
THE KIT
Not only a Network, made of software, also a hardware Kit! Resilient, sustainable, portable to survive and connect everywere!
You can make it yourself or support oasis-project and buy it here
SELF HOSTED & ENCRIPTED
Local Activation
OASIS runs directly on your Linux system. When started, it launches your browser into a locally hosted node interface.

Hack the planetMarkdown-Based Frontend
The entire user interface is based on Markdown rendering, making it one of the most auditable, minimal and secure UIs.

Offline & Replication Recovery
Each user replicates content they support. If your node is lost, you can recover your content through trusted peers.

Cryptographic Feed Integrity
All the content is signed using Ed25519. Every post, connection or interaction is verifiable and immutable.
HACK THE PLANETDISTRIBUTED
Scuttlebutt Protocol
Based on append-only logs, where each peer maintains a personal chain of content replicated via trust.

Scuttlebut was released in 2017 and presented in the CCC
Gossip Communication
Data propagates peer-to-peer through the Gossip protocol, ensuring high fault-tolerance and antifragility.

Modular Plugin Architecture
Extendable via plugins such as torrents, WebRTC video calls, PDF renderers and more. All using secure JavaScript modules.
Non-indexed Trustnet
There is no search engine to find every user, you can only view the habitants you support

PUBs act as community mirrors with HTTPS frontends, making content accessible from the clearnet while preserving protoco>
Each PUB is a sovereign node. Federation exists only as a convenience layer, not a point of control.
BLOCKCHAIN FOR THE PEOPLE
Unmutable Data
Replicability enabled by blockchain ensures that once data is recorded, it remains consistent and available across all nodes, making tampering virtually impossible.

Ecoin
ECOin is a crypto-currency with the goal of providing a long-term energy-efficient digital economy strategy.

It uses -SCRYPT algorithm- and implements 3 different mining systems.
Proof-Of-Work
Proof-Of-Stake
Proof-Of-Transaction
There is no maximum number of coins, through the estimated coinbase size will be roughly 225 million ECO.